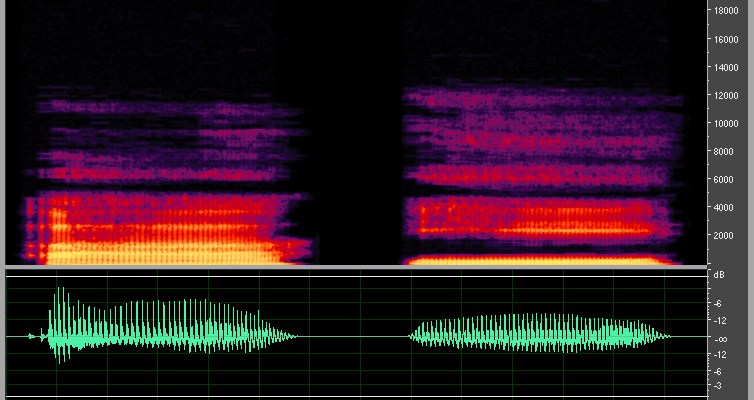
This peculiar malware, which can transmit infected files using the speaker and microphone systems of machines, could cross the air-gap that protects systems against potential infection.
Several weeks ago, security researcher Dragos Ruiu publicly revealed the potential propagation of a type of malware between the computers in his laboratory via a medium that has been quite uncommon up to this point: the air. Preliminary investigation of this bug, which as been dubbed badBIOS, have determined a sophisticated method of transmitting infected files using the speaker and microphone systems of machines as a medium to propagate the useful loading of malware through sound.
Following the detection of this malware, researcher Dragos Ruiu has spent several years investigating badBIOS, and based on his preliminary conclusions, it is very similar to other rootkits that prevent users from deleting them until system start-up is blocked from the physical disk. Despite the initial disbelief of some security experts, a team of scientists at the Franuhofer Institute has published an article that demonstrates that malware can cross what up until now was thought to be an infallible barrier, the air-gap or complete isolation of a system from other less-secure networks as an extreme measure to protect the system against potential infection.
For the demonstration of how badBIOS can cross the air-gap and transmit information from the speakers of a computer, to be recorded by the microphone of an isolated system, researchers were able to ping the signal propagated by a modem defined by software based on the GNU Radio Project, from one system to another with transfer ranges of up to 19.7 metres between machines.
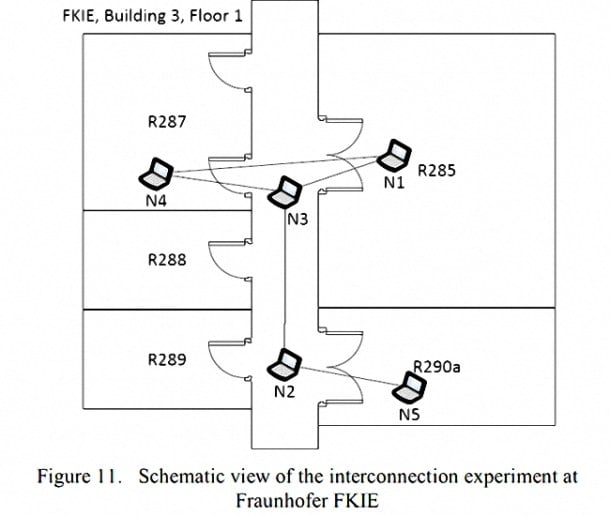
Obviously the transfer rate is relatively low, barely 20 bits per second, which would delay the transmission of data between four computers by up to 18 seconds, but Ruiu warns that badBIOS is one of the first visible stages of this peculiar malware, which could affect Windows, OSX, Linux and BSD in the future.
However, scientists also say that it is possible to block the malware attack by implementing an electronic filter that allows a specific range of frequencies of a signal to pass, but blocks other sounds below a specified threshold. However, it would also suffice to configure computers to work only with headphones –with no microphones– or simply remove the speakers from the system.
Despite the fact that this type of malware requires additional software or keyloggers for the attack to be truly effective, it is also true that the small amount of information that is transmitted makes prior detection virtually impossible. In other words, any foreign sound from the speaker of a computer at any time during the day could be interpreted as possible interference between machines in the laboratory or the presence of a mobile phone nearby.
Luckily, the propagation of this type of malware through sound is very specific and is not a widespread problem that we need to worry about, although we always have the option of getting rid of the computer’s speakers and microphone and using an iPod to listen to music while we work.
Images | via wikipedia